Aws the Specified Vpc Has No Internet Gateway Attached update the Vpc and Then Try Again
In this tutorial we'll go through the steps to create an AWS VPC (Virtual Private Cloud) with public and individual subnets, and enable outbound internet access from the private subnets through a NAT (Network Address Translation) Gateway.
We'll exist using the AWS Management Console (https://aws.amazon.com/console/) to perform all of the steps in the tutorial, the AWS Console can be a bit more than transmission than some other options (due east.g. AWS CLI, CloudFormation, Terraform etc) but I observe it helpful when learning to go a better understanding of all the pieces involved and how they fit together.
Tutorial Contents
- Create AWS VPC (Virtual Individual Cloud)
- Create Public and Individual Subnets
- Create Internet Gateway (IGW)
- Create NAT Gateway
- Configure Route Tables
- Remove everything from AWS (Make clean up)
Create AWS VPC (Virtual Private Deject)
An AWS VPC is a virtual private network in the AWS Cloud where you can provision and run dissimilar AWS resources (east.k. ECS container instances, Lambda functions, RDS database instances etc).
For more info on AWS VPC see https://docs.aws.amazon.com/vpc/latest/userguide/what-is-amazon-vpc.html.
Follow these steps to create your VPC:
- Sign into the AWS Direction Panel at https://aws.amazon.com/console/. If you don't take an account yet click the Create a Free Account button and follow the prompts.
- Go to the VPC Service section and select Your VPCs in the left menu.
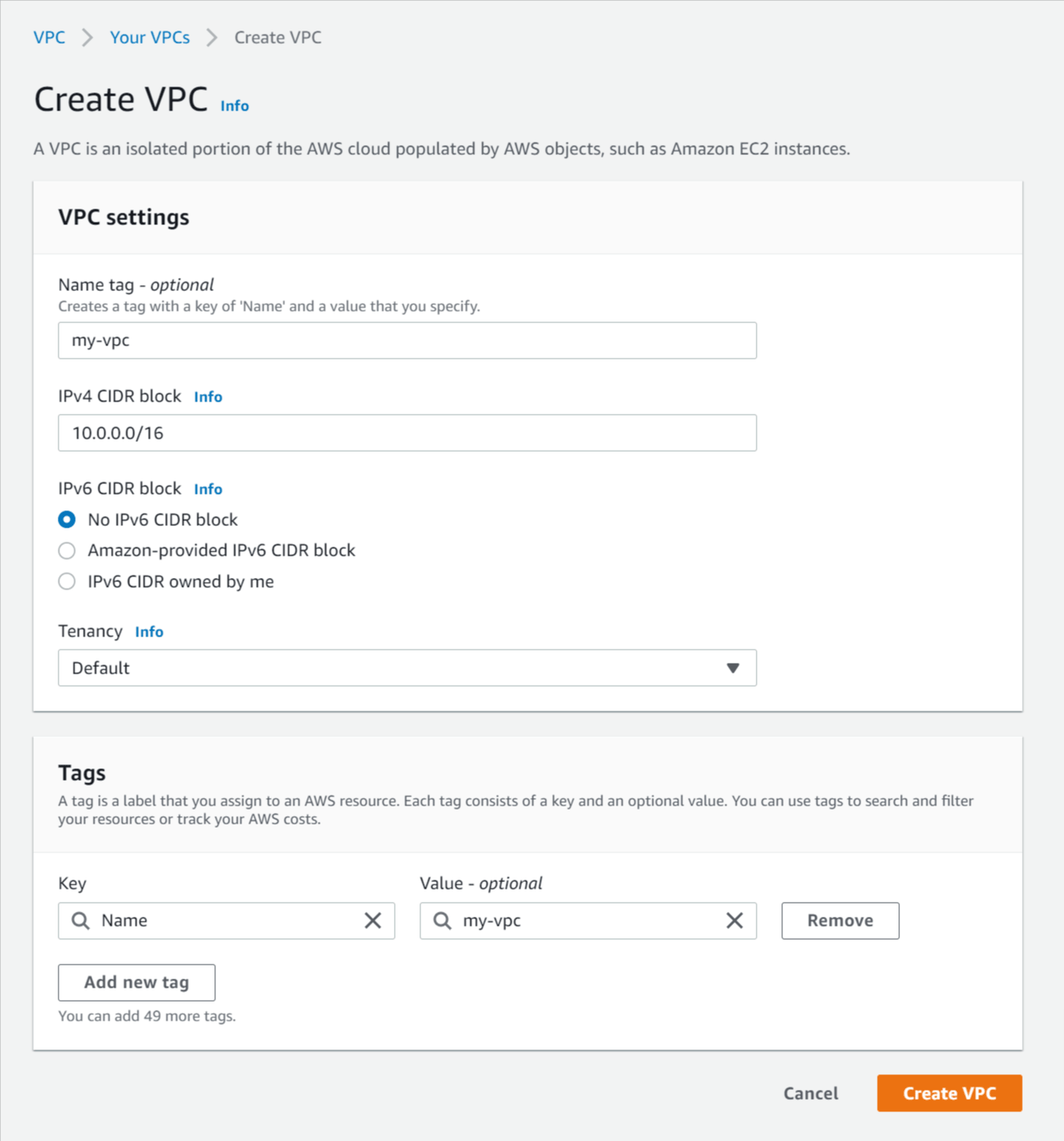
- Click Create VPC and enter the following details:
- Name tag - Enter a proper name for the VPC (e.g. my-vpc).
- IPv4 CIDR block - Enter a CIDR block to specify the IP address range available for the VPC. If you lot're non sure what to put you lot can enter 10.0.0.0/xvi which specifies the IP address range from x.0.0.0 to 10.0.255.255, giving your VPC up to 65,536 IP addresses.
For more info on CIDR notation and IP addressing encounter https://www.digitalocean.com/customs/tutorials/understanding-ip-addresses-subnets-and-cidr-notation-for-networking. - IPv6 CIDR block - No IPv6 CIDR block.
- Tenancy - Default.
- Click Create VPC.
Step screenshots:
Create VPC
Back to elevation
Create Public and Private Subnets
Next nosotros'll create the subnets inside our VPC that volition hold our AWS resources.
Public vs Private subnets
Subnets can be public (attainable from the internet) or individual (non accessible from the net), a subnet is public when it routes traffic through an Internet Gateway (IGW) attached the VPC. A subnet is private when it doesn't route traffic through an IGW, nonetheless outbound net admission can be enabled from a private subnet by routing traffic through a Network Address Translation (NAT) Gateway located in a public subnet.
For more info on AWS Subnets see https://docs.aws.amazon.com/vpc/latest/userguide/VPC_Subnets.html.
Subnets in multiple AZs
We'll create two public and two private subnets so each subnet type can comprehend multiple AZs (Availability Zones), this is required by some AWS resources (e.g. RDS databases) and is recommended by others (e.g. Lambda functions).
Follow these steps to create the subnets in your VPC:
- Select Subnets in the left menu.
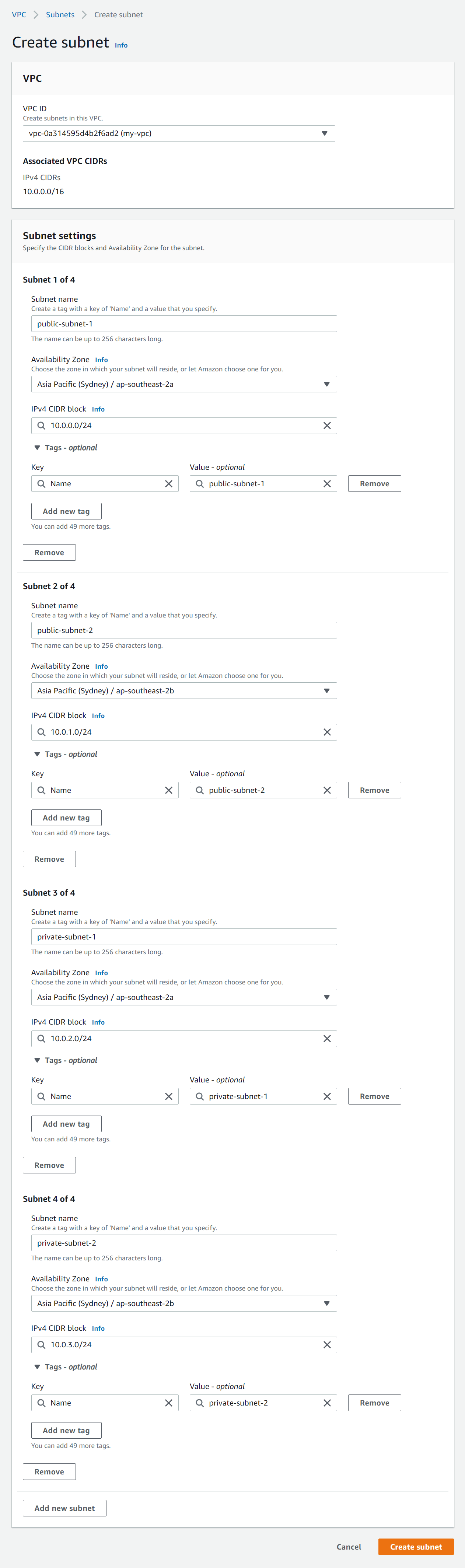
- Click Create subnet and enter the following details:
- VPC ID - Select the VPC yous created above.
- Subnet settings - Click Add new subnet iii times to brand four new subnet forms.
- Subnet one of 4 - Enter the post-obit details:
- Subnet name - Enter public-subnet-1
- Availability Zone - Select the showtime pick (e.1000. ap-southeast-2a)
- Enter a CIDR block for each subnet that fits into your VPC CIDR block (e.g ten.0.0.0/24)
- Subnet ii of 4 - Enter the following details:
- Subnet name - Enter public-subnet-2
- Availability Zone - Select the 2nd selection (e.yard. ap-southeast-2b). This must be in a different AZ to public-subnet-1.
- Enter a CIDR block for each subnet that fits into your VPC CIDR cake (e.g 10.0.1.0/24)
- Subnet 3 of four - Enter the post-obit details:
- Subnet proper noun - Enter individual-subnet-1
- Availability Zone - Select the first pick (eastward.thou. ap-southeast-2a)
- Enter a CIDR block for each subnet that fits into your VPC CIDR cake (e.g 10.0.ii.0/24)
- Subnet four of 4 - Enter the following details:
- Subnet name - Enter individual-subnet-2
- Availability Zone - Select the second selection (e.yard. ap-southeast-2b). This must be in a dissimilar AZ to private-subnet-1.
- Enter a CIDR block for each subnet that fits into your VPC CIDR block (e.1000 x.0.3.0/24)
- Click Create subnet
Pace screenshots:
Create subnets
Back to top
Create Internet Gateway (IGW)
An AWS internet gateway (IGW) is used to enable internet admission to and from subnets in your VPC. A subnet that routes traffic to an IGW is a public subnet, and a subnet that doesn't route traffic to an IGW is a individual subnet. Routes are configured in route tables that nosotros'll cover before long.
For more on internet gateways see https://docs.aws.amazon.com/vpc/latest/userguide/VPC_Internet_Gateway.html.
Follow these steps to create an IGW and attach it to your VPC:
- Select Net Gateways in the left menu.
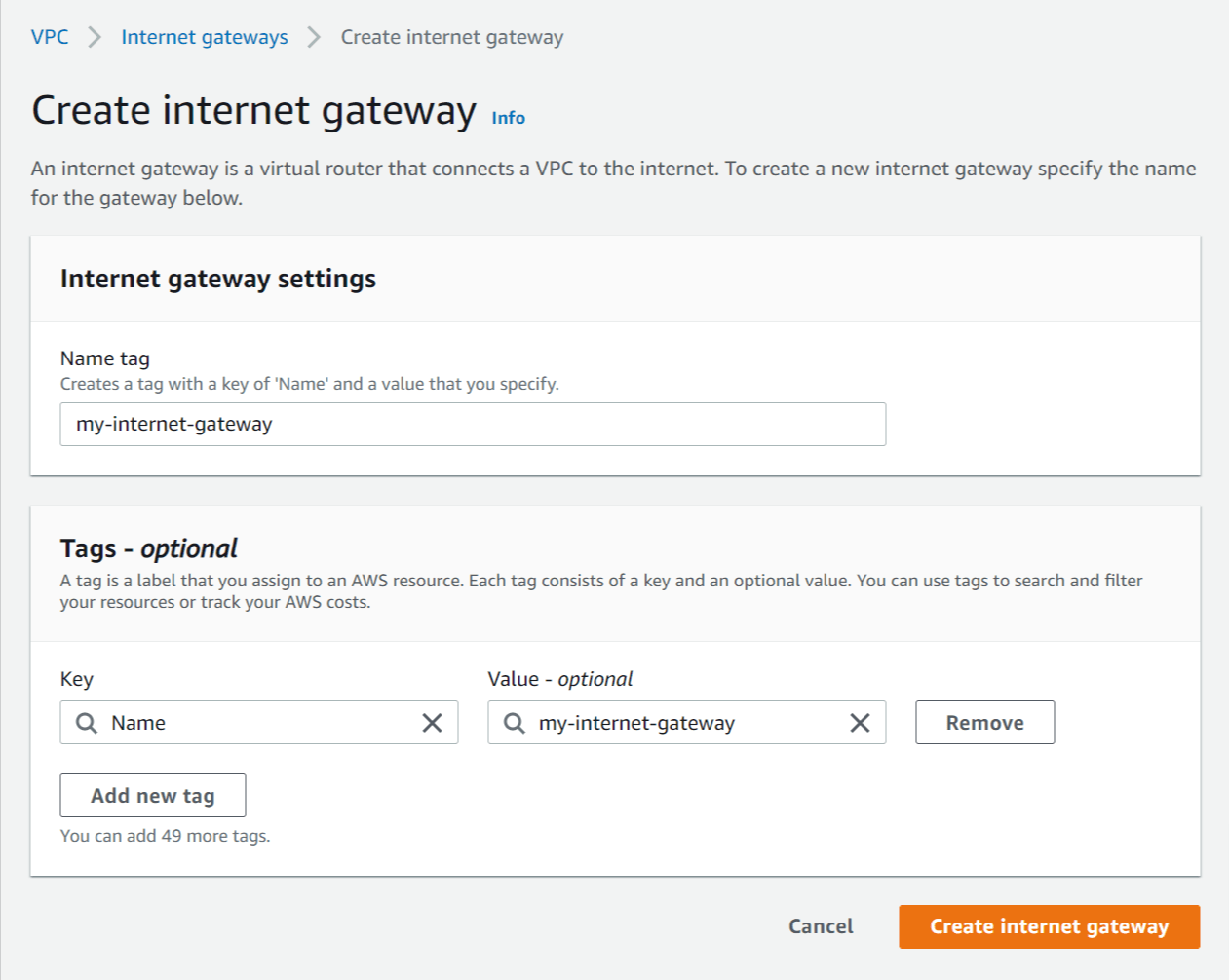
- Click Create internet gateway and enter the following details:
- Name tag - Enter a name for the internet gateway (e.g. my-internet-gateway).
- Click Create internet gateway.
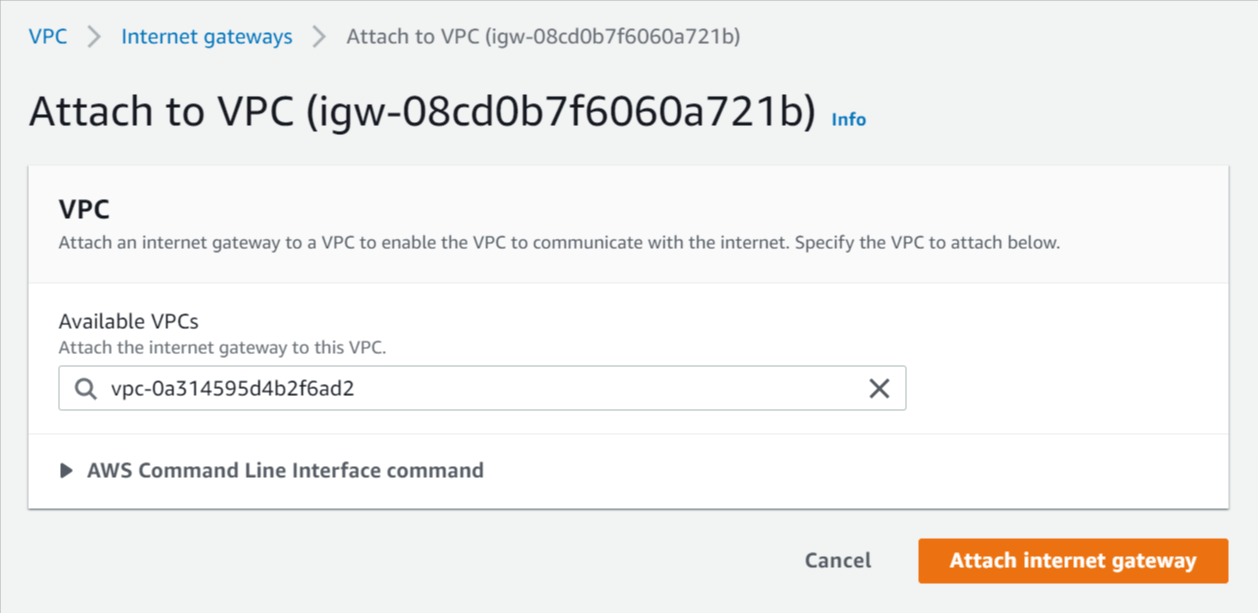
- Select Actions -> Attach to VPC.
- Select the VPC you created above and click Attach internet gateway.
Step screenshots:
Create internet gateway
Attach cyberspace gateway
Back to acme
Create NAT Gateway
A network accost translation (NAT) gateway is used to provide outbound internet access to AWS resources running in private subnets. A NAT gateway is located in a public subnet and acts similar a proxy for outbound traffic from private subnets that road their traffic to the NAT gateway.
For more info on NAT gateways see https://docs.aws.amazon.com/vpc/latest/userguide/vpc-nat-gateway.html.
Follow these steps to create a NAT gateway in your public subnet:
- Select NAT Gateways in the left menu.
- Click Create NAT gateway and enter the post-obit details:
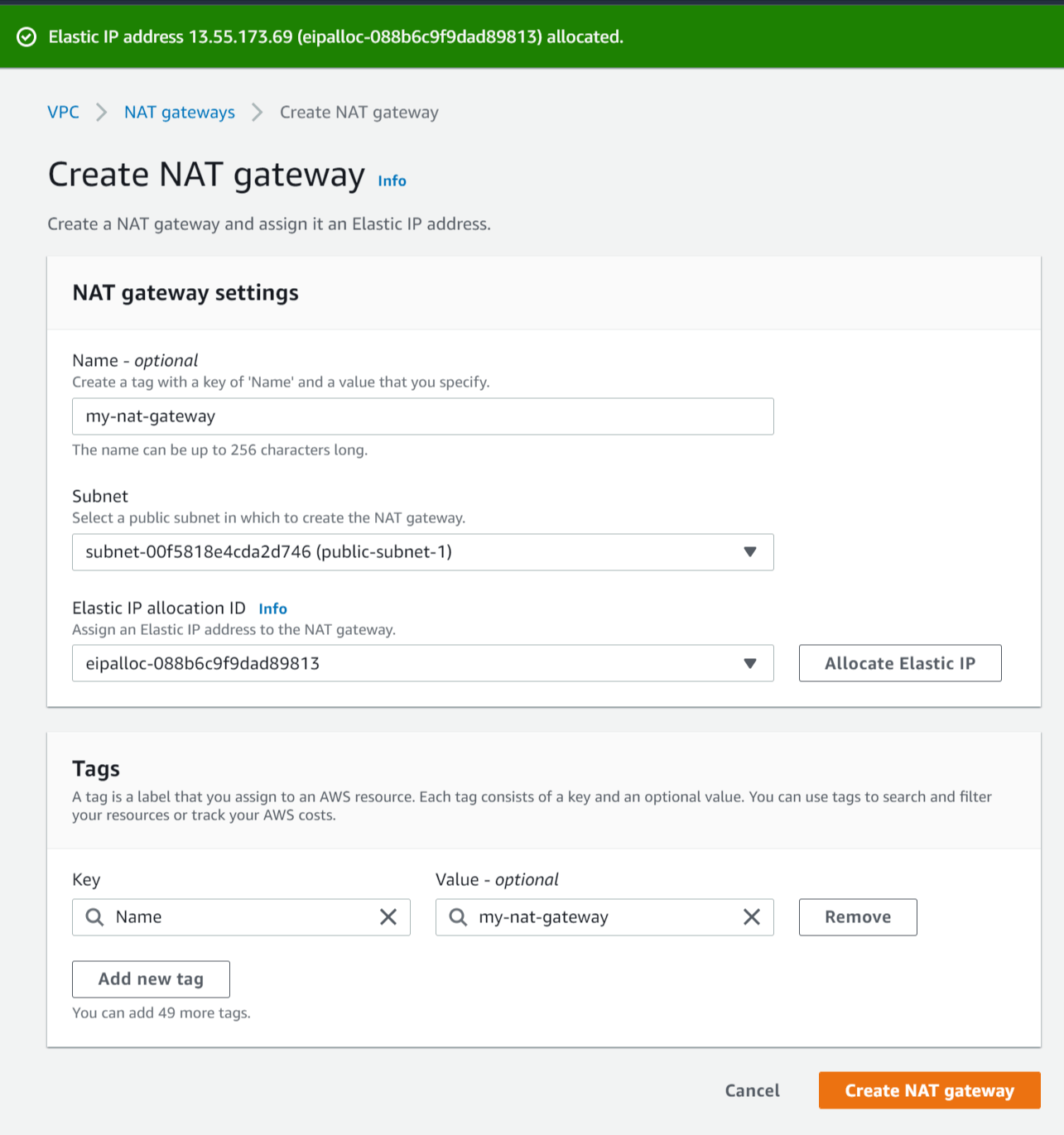
- Proper name - Enter a proper noun for the NAT gateway (e.g my-nat-gateway).
- Subnet - Select the subnet with the name public-subnet-1.
- Elastic IP resource allotment ID - Click Allocate Elastic IP to create a new elastic IP for the NAT gateway.
- Click Create NAT gateway.
Step screenshots:
Create NAT gateway (later on allocating rubberband IP)
Back to top
Configure Route Tables
Route tables are used to command where network traffic is routed from subnets. Each VPC has one Main road tabular array that is used by default for any subnet that isn't explicitly associated with a route table.
For more on AWS route tables see https://docs.aws.amazon.com/vpc/latest/userguide/VPC_Route_Tables.html.
Configure VPC main route table to exist individual
Here we'll configure the principal road table in the VPC to target the NAT gateway to make subnets private by default. A individual subnet is not accessible from the internet merely can exist given outbound internet access via a NAT Gateway located in a public subnet.
Follow these steps to configure the VPC primary road table to be individual:
- Select Route Tables in the left menu.
- Select the principal route table for the VPC you created higher up.
- Hover the mouse over the Proper name column of the selected road table, so click the edit icon and enter the proper noun chief-route-tabular array.
- Click the Routes tab below and click Edit routes.
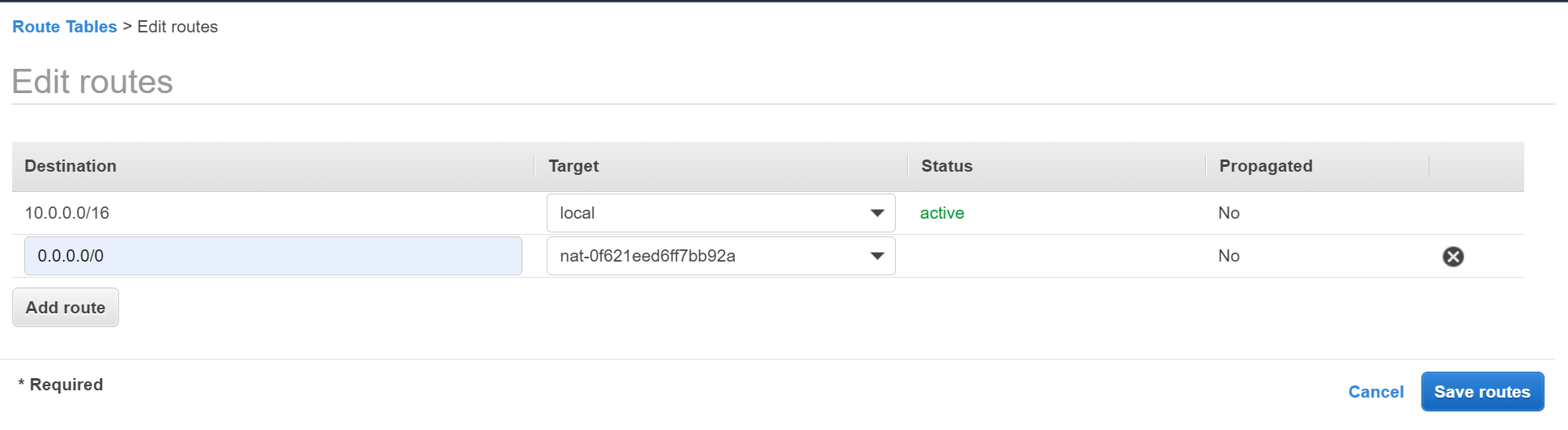
- Click Add together route and enter the following details:
- Destination - Enter 0.0.0.0/0 to match all not-local traffic.
- Target - Select NAT Gateway then select the NAT gateway yous created to a higher place.
- Click Save routes.
Step screenshots:
Add route to NAT gateway
Create new route table for public subnets
Here we'll create a new route tabular array that targets the cyberspace gateway (IGW) that will be used by public subnets. A public subnet is accessible from the cyberspace by being associated with a route table that targets an IGW.
Follow these steps to create a route table and associate it with public subnets:
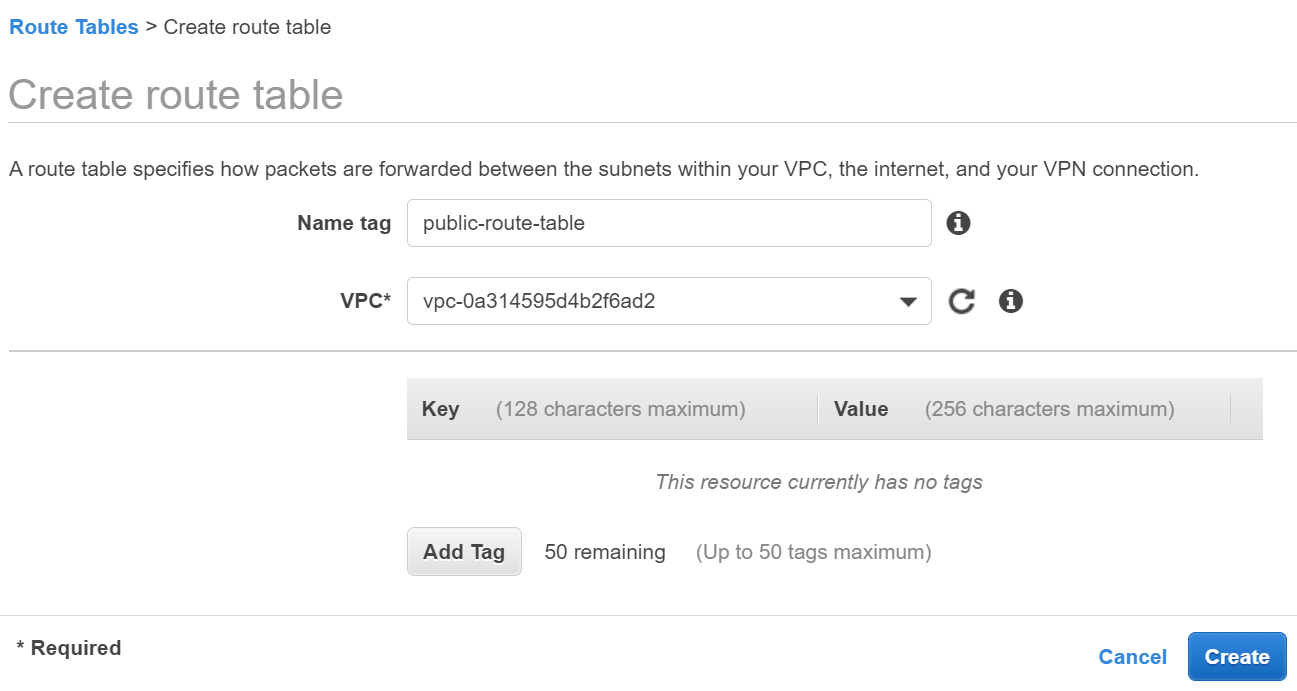
- Click Create route table and enter the following details:
- Name tag - Enter a proper name for the route table (eastward.m. public-route-table).
- VPC - Select the VPC you lot created above.
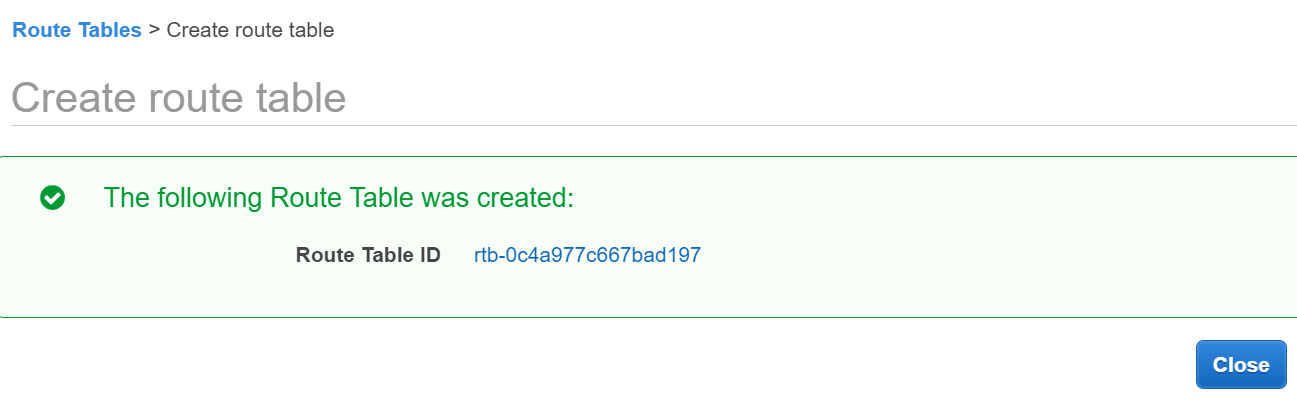
- Click Create then click the link displayed with the new route table ID.
- Click the Routes tab and Edit routes.
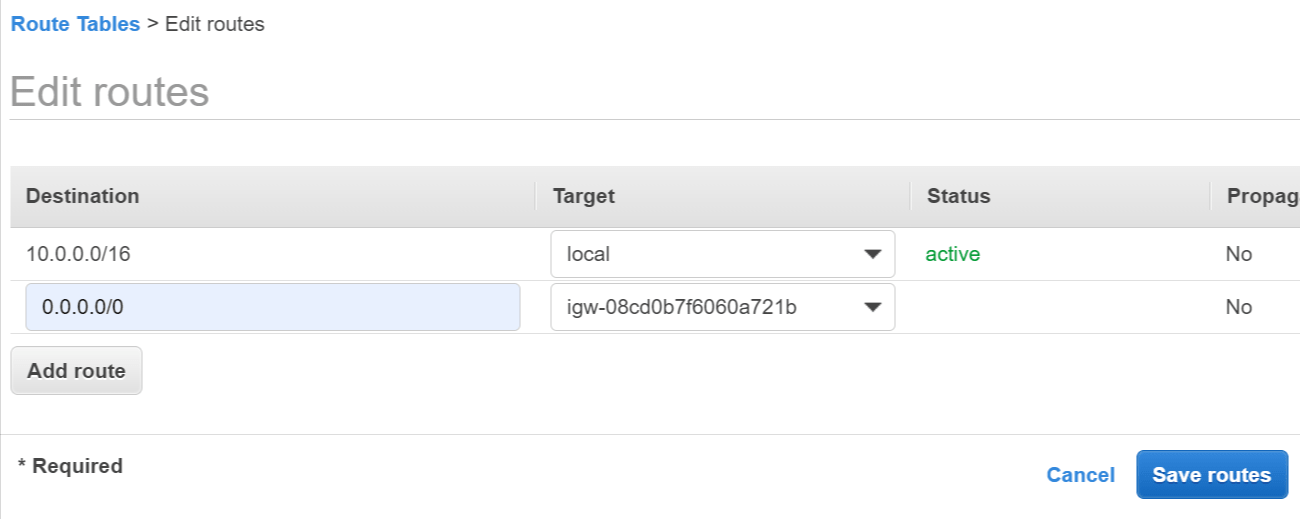
- Click Add route and enter the following details:
- Destination - Enter 0.0.0.0/0 to match all non-local traffic.
- Target - Select Internet Gateway then select the internet gateway you created above.
- Click Save routes.
- Navigate dorsum to the Route tables listing and select the public-route-tabular array you simply created.
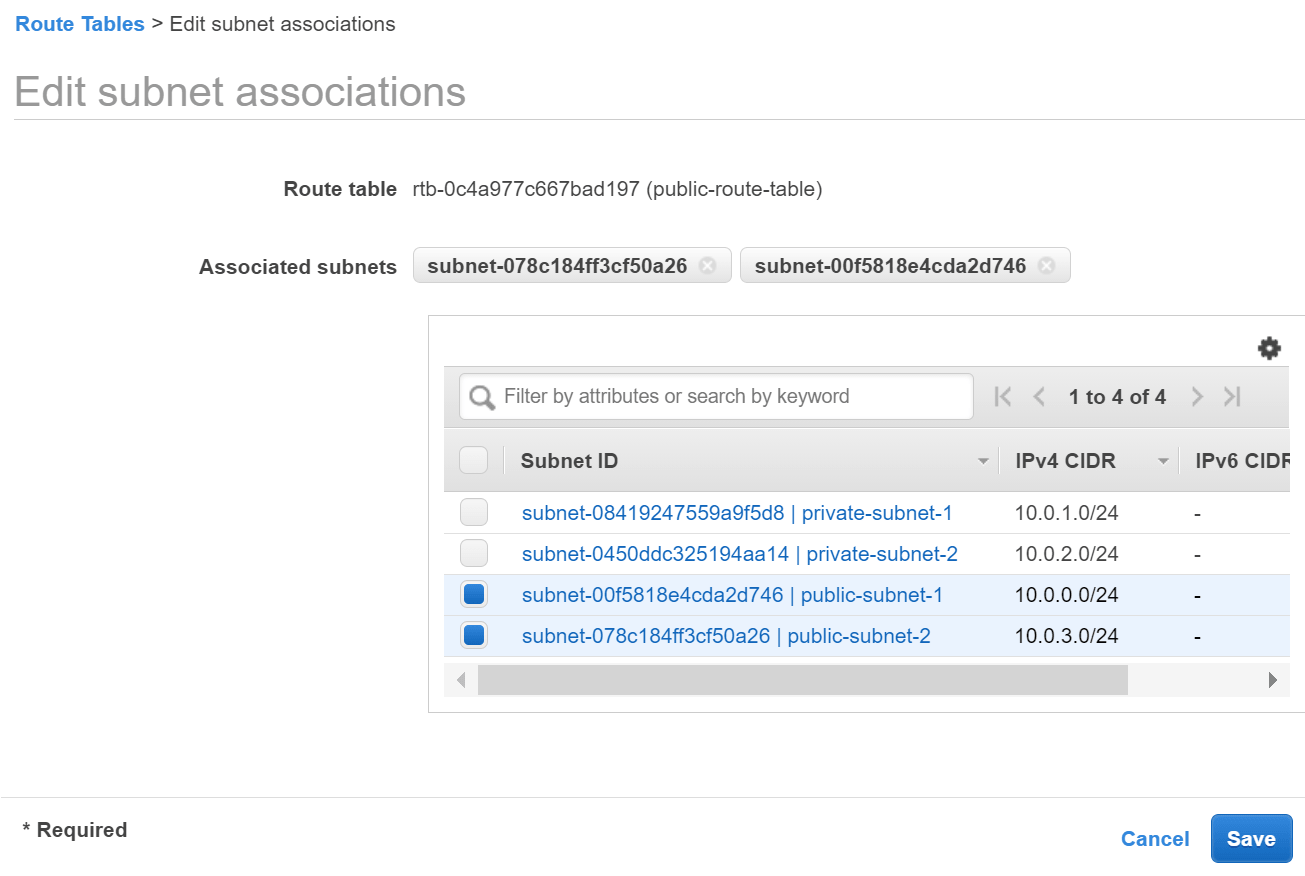
- Click the Subnet Associations tab and Edit subnet associations.
- Select the subnets named public-subnet-i and public-subnet-2 and click Salvage.
Stride screenshots:
Create road tabular array
Click link with the new route table ID
Add route to cyberspace gateway (IGW)
Acquaintance road table with public subnets
Back to top
Remove everything from AWS (Clean up)
When you're finished you lot tin can remove/delete all of the AWS resources created in the tutorial to avoid incurring whatsoever unnecessary costs.
Follow these steps to clean upwards the resources created in AWS:
Delete NAT Gateway
- Get to the VPC Service section and select NAT Gateways in the left menu.
- Select the NAT gateway created above (my-nat-gateway) and click Actions and Delete NAT gateway.
- Enter delete into the confirmation text field and click Delete.
Release Elastic IP
- Afterward the NAT gateway is deleted select Rubberband IP addresses in the left bill of fare.
- Select the IP accost that was allocated to the NAT gateway, click Actions and Release Elastic IP address.
Delete VPC
- Select Your VPCs in the left carte du jour.
- Select the VPC you created at the start of the tutorial (my-vpc) and click Deportment and Delete VPC.
- Enter delete into the confirmation text field and click Delete.
Dorsum to elevation
Subscribe to my YouTube channel or follow me on Twitter, Facebook or GitHub to be notified when I mail service new content.
I'thou currently attempting to travel effectually Commonwealth of australia past motorcycle with my married woman Tina on a pair of Royal Enfield Himalayans. Y'all can follow our adventures on YouTube, Instagram and Facebook.
Source: https://jasonwatmore.com/post/2021/05/30/aws-create-a-vpc-with-public-and-private-subnets-and-a-nat-gateway
0 Response to "Aws the Specified Vpc Has No Internet Gateway Attached update the Vpc and Then Try Again"
Post a Comment